

Enterprise Networking Planet content and product recommendations are editorially independent. We may make money when you click on links to our partners. Learn More.
As the number of cyber attacks on organizations continues to rise, organizations must take necessary measures to protect their systems and networks. One such measure often used by organizations is the firewall. However, deploying firewalls without an effective firewall policy can be counterproductive for any organization.
A good firewall policy helps organizations determine which traffic is allowed or blocked from entering or leaving a network. In this article, we will discuss what makes up a great firewall policy design, how you can configure a firewall policy, and what a firewall template should look like.
Table of Contents
An effective firewall policy should be a blueprint that follows firewall best practices on how an organization’s firewalls should handle inbound and outbound network traffic for specific IP addresses and address ranges, applications, and protocols based on the organization’s overall information security policies.
Below are some basics of a firewall policy design.
It’s crucial to first identify your organization’s security objectives before venturing into firewall policy design. This is because a firewall policy should not just speak to your unique security needs but also comply with the organization’s general security policy.
Identifying your organizational security objectives should factor in the types of traffic that need to be allowed or blocked, compliance requirements, resource allocation, and their impact on the overall business objective.
Firewall architecture refers to the design and layout of a firewall system responsible for controlling and monitoring network traffic. Defining your firewall architecture will involve deciding on the type of firewall to be used, the location of the firewall within the network, and the number of firewalls required to achieve the desired level of security in the organization.
Different types of firewalls are available, such as packet-filtering firewalls, stateful firewalls, and next-generation firewalls. Each type has its strengths and weaknesses, so choosing the right one will depend on your organization’s specific security requirements.
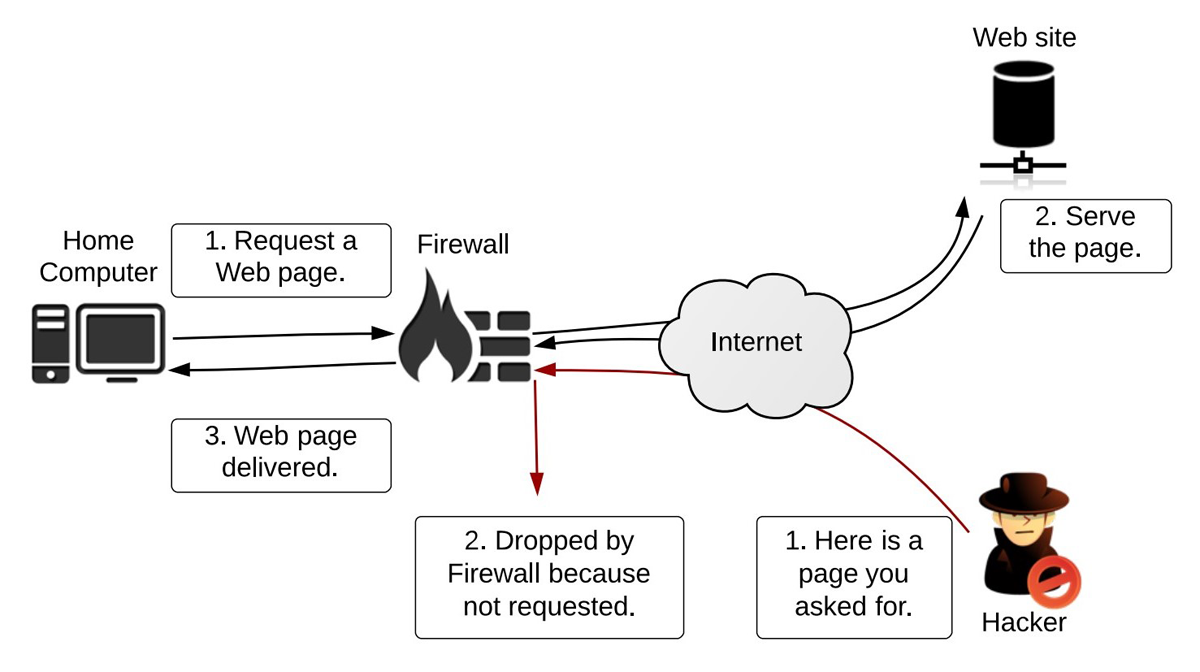
Firewall rules are the specific instructions that determine which traffic is allowed or blocked based on criteria such as source and destination IP addresses, ports, protocols, and application types.
When creating firewall rules, it is vital to be as specific as possible to minimize the risk of false positives. Rules should be written in plain language so they are easy to understand and maintain.
Monitoring your firewall is essential to ensuring that it’s working effectively. This includes regularly reviewing logs and alerts, analyzing network traffic, and testing your firewall for vulnerabilities.
Besides monitoring logs and analyzing network traffic, monitoring your firewall also involves ensuring that people within the organization follow and implement the firewall security rules in the policy. In addition, regular monitoring will help you to quickly identify and respond to potential network security threats before they can cause significant damage to the organization.
There are several ways to configure a firewall policy, which will depend on the organization’s security needs, the type of firewall, and the expertise of the network administrator. Below are some of the approaches you can adopt to configure your firewall policy.
A port-based firewall policy configuration focuses on controlling network access based on the traffic’s communication ports. In this method, firewall rules are based on specific network ports used to identify the type of traffic.
For instance, web traffic typically uses port 80 or 443, while email traffic typically uses port 25 or 587. Based on this, port-based firewalls can be configured to allow or block traffic based on the source and destination ports used by the traffic.
![]()
In this firewall configuration method, the focus is on configuring the firewall to allow or block traffic based on the protocol used, such as Transmission Control Protocol (TCP), User Datagram Protocol (UDP), or Internet Control Message Protocol (ICMP). This configuration can be done by specifying rules that define which traffic should be allowed or blocked based on the protocols used.
Firewall configuration can also be based on specific IP addresses, such as blocking traffic from a known malicious IP address or allowing traffic only from trusted sources. This method can take the form of identifying countries with a high percentage of malicious IP addresses and configuring your firewall to block all IPs from such countries.
Some advanced firewalls can be configured to analyze the behavior of network traffic and identify patterns or anomalies that may indicate a security threat. In this configuration, the firewall software monitors all activities on the organization’s network to identify and treat any deviation from the normal pattern as a threat.
In this configuration, the firewall is configured to recognize and block specific applications, such as instant messaging or peer-to-peer file-sharing programs largely considered malicious.
In this method, the firewall identifies application signatures and decides whether or not to permit, deny, or redirect the traffic from such applications.
There are different types of firewall policies that organizations can adopt. Some of the notable ones include hierarchical, global network, and regional network firewall policies.
A hierarchical firewall policy allows for more granular and efficient network traffic control. In this approach, firewall rules are grouped into a hierarchy or a tree-like structure where each level of the hierarchy represents a specific security zone or policy domain.
Hierarchical firewall policies enable the creation and implementation of a uniform firewall policy throughout your organization. These policies can be assigned to the entire organization, different zones, or policy domains.
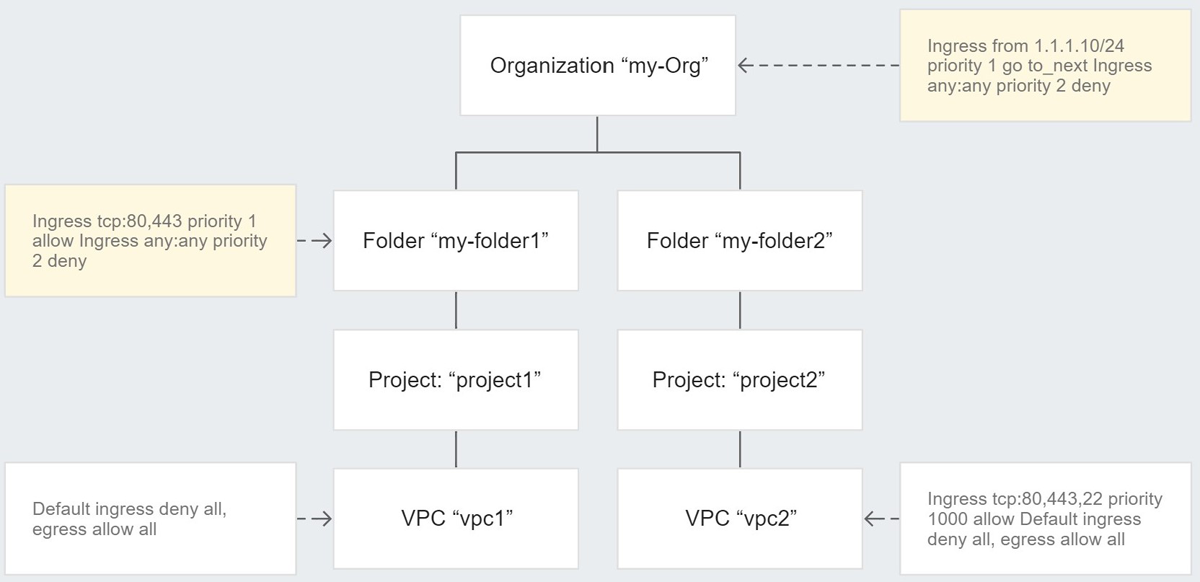
With global network firewall policies, organizations can group rules into a policy component applicable to all regions or zones. This policy applies to all devices and systems within the network, regardless of their location or function. The global policy provides a consistent level of security across the entire network and helps to prevent unauthorized access, data breaches, and other security threats. The global policy can be managed centrally and is typically enforced by a dedicated firewall device or software solution.
A regional network firewall policy is a set of rules that govern how traffic is allowed or blocked within a specific geographical area of a network. Unlike the global firewall policies that apply automatically to all regions of the network, the regional network firewall policies allow organizations to categorize firewall rules into policy objects that are targeted at specific regions.
The regional policy can be customized to meet these specific needs while still adhering to the overall global policy of the organization. Regional firewall policies are usually managed by local IT teams and are enforced by dedicated firewall devices or software solutions within each region.
While drafting an excellent firewall policy for your organization requires some expertise in network administration, vulnerability, and security compliance, a good example can also make things easier for you when faced with the task of drafting one. Below are two examples you can take some cues from.
This University of Connecticut firewall policy is a basic firewall policy published on their webpage. The policy defines the essential rules regarding managing and maintaining firewalls at the University of Connecticut and who is bound to comply with this firewall policy.
Although this is a basic example of a typical firewall policy, it captures some key aspects of a firewall policy, such as firewall rules, firewall configuration standards, defining the policy’s purpose, and how any violation will be handled.
Unlike the University of Connecticut, the firewall policy from Texas Wesleyan University goes into more detail in the definition of terms applied in the policy and provides more comprehensive guidelines for each section of the policy.
As mentioned above, policies are also determined by the specific needs of an organization, and in this example, the policy covers Texas Wesleyan networks, whether managed by employees or by third parties, and all firewalls owned, rented, leased, or otherwise controlled by Texas Wesleyan employees. Notable additions to the Texas Wesleyan example include Firewall Physical Security, Demilitarized Zones (DMZ), Virtual Private Networks (VPNs) sections, and more.
A well-designed and properly configured firewall policy is critical for protecting an organization’s network and sensitive information from unauthorized access, malware, and other security threats.
Network administrators can create a robust firewall policy that balances security needs with operational requirements by following best practices and adopting real-world examples.
Regular reviews and updates to the policy are also essential to ensure that it remains effective against evolving threats.
With a comprehensive firewall policy in place, organizations can significantly reduce their risk of data breaches, network downtime, and other security incidents, helping to maintain their reputation and trust with customers, partners, and stakeholders.
Don’t forget to view or download our Firewall Policy Template. And improve your firewall protection further with these firewall best practices.